Intervalid ISMS actively supports you in the implementation of your clients' projects. The latest technology, excellent usability and a structured design are the foundation for a fast and efficient ISMS implementation. All the process steps necessary for the rollout of a specific policy are mapped in one system per client, with the respective clients separated from each other on the system. Through regular monitoring, you can keep track of your client projects and are prepared for certifications.
The structured all-in-one solution includes:
The software includes all mandatory documents for a certification according to ISO 27001 & further helpful documents.

Our tool optimally supports you in implementing the NIS-2 directive.
Automation and functionality save time, significantly improve security and increase productivity.
Contact us for a live demo, a free trial or your personalized offer.
*TISAX® is a registered trademark of the ENX Association. Intervalid GmbH has no business relationship with ENX. The naming of the TISAX brand is not associated with any statement by the brand owner on the suitability of the service advertised here.
With Intervalid ISMS, you gain a secure all-in-one solution to simplify the complex topic of information security within your company. The software helps you save time, money, human resources, and stress. Intervalid ISMS prepares you for certifications according to standard norms such as ISO 27001, BSI IT-Grundschutz, VdS 10000, TISAX®, CISIS12®, B3S, and more.
NIS-2 – All updates of the NIS-2 Directive are included.
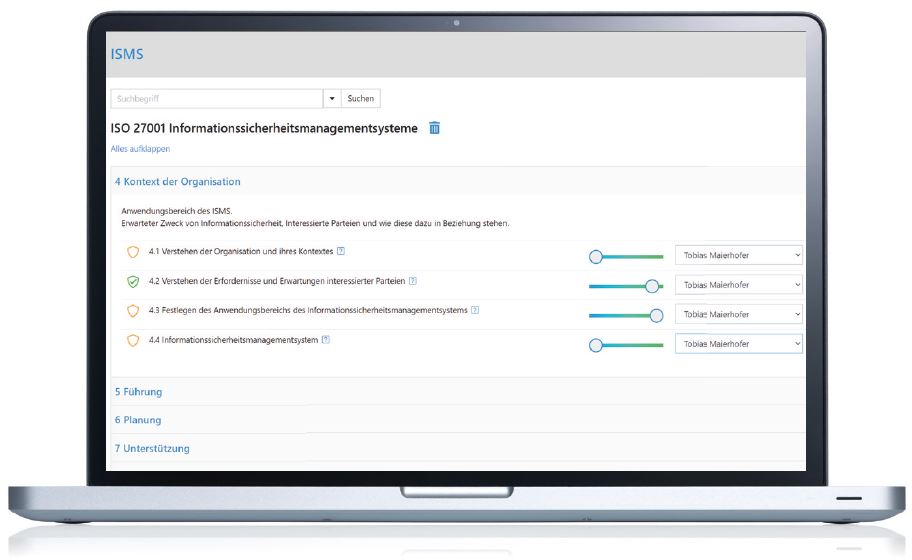
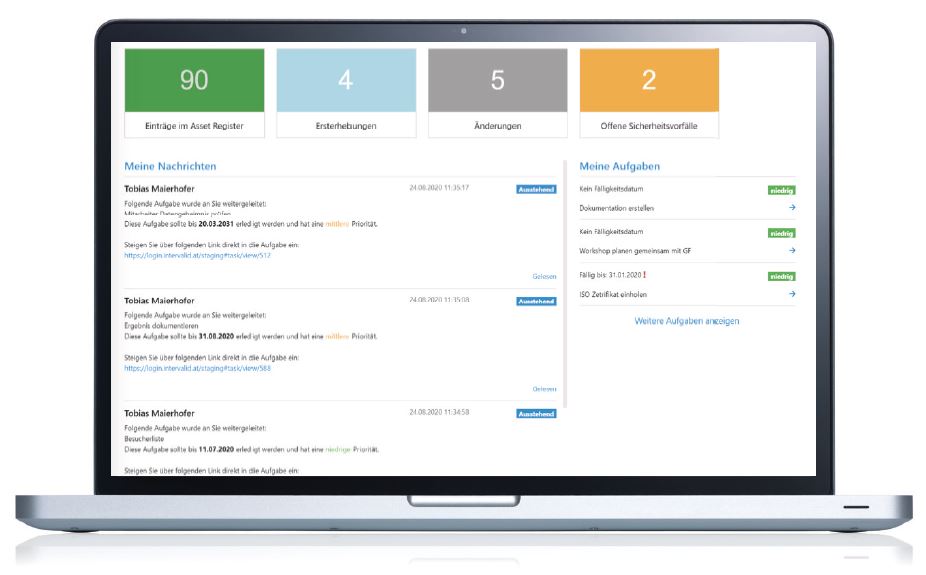
When implementing an ISMS, the cooperation of all departments is crucial for success: Set tasks, including deadlines, and distribute them to the responsible employees at your client company. Each user has their own task list, and the current project status is visible at all times. This means all employees are actively involved in the process.
To minimize security risk within the company, employees must be made aware of both the risks and the appropriate procedures they are required to follow. To achieve this, sample templates are available to create the necessary policies and processes for the organization. These form the foundation for ISMS implementation, as they will be followed by all employees. The documents should be regularly maintained and kept up to date, to ensure consistent and structured implementation.
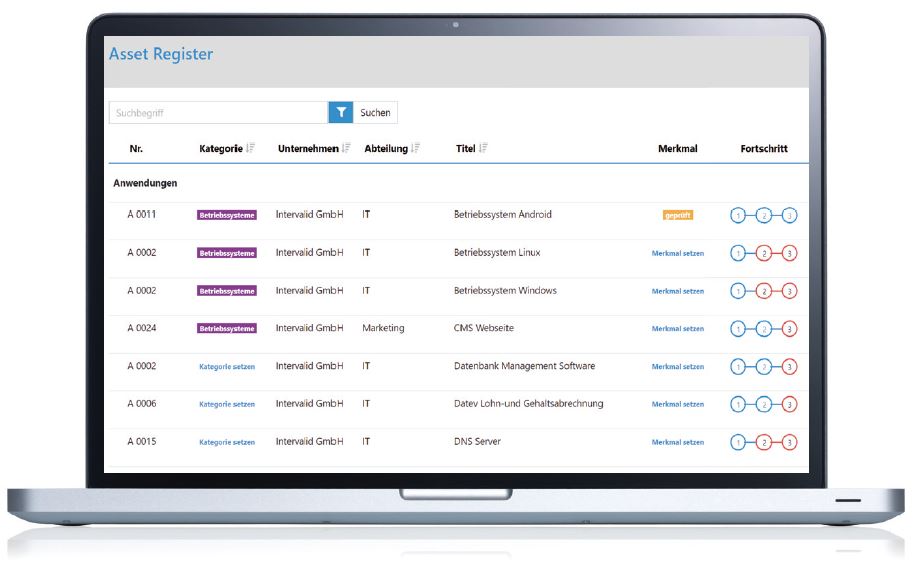
This function allows you to capture and group assets in a structured register. To make this process as efficient as possible, you can either use a template or import the data. You will need to define a responsible person (owner) for each asset. The workflow can then be used to log new assets or to report changes to existing ones. The technical and organizational measures (TOMs) can be set out either via a template or in a personalized form according to your needs. The register is clear, multilingual, and easy to use, as well as offering customizable selection options.
This is where the level of protection for each asset is determined. Business-critical assets, particularly those of high importance to the company in terms of information security, are identified. The responsible employee assesses the protection level required for each asset with the help of predefined risk levels. This lays the foundation for the risk analysis.
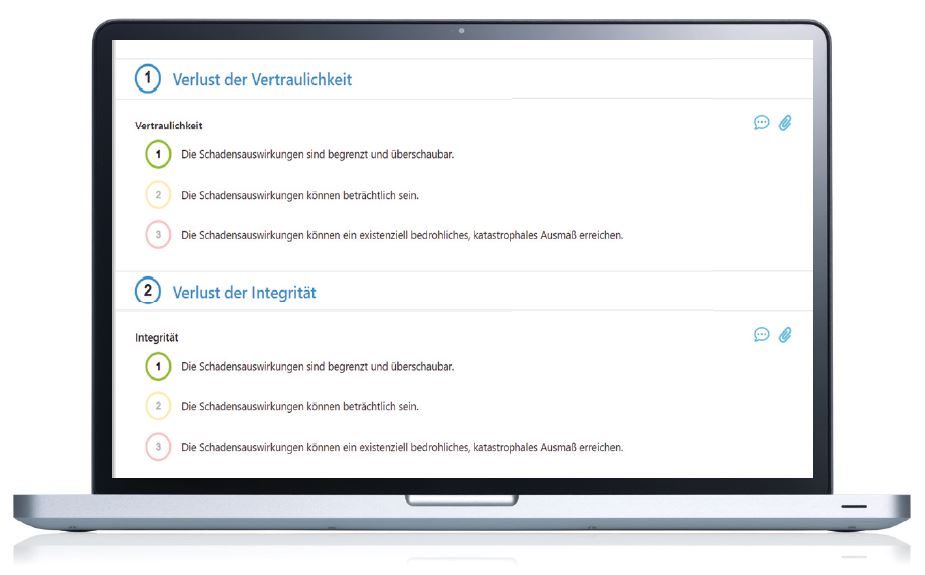
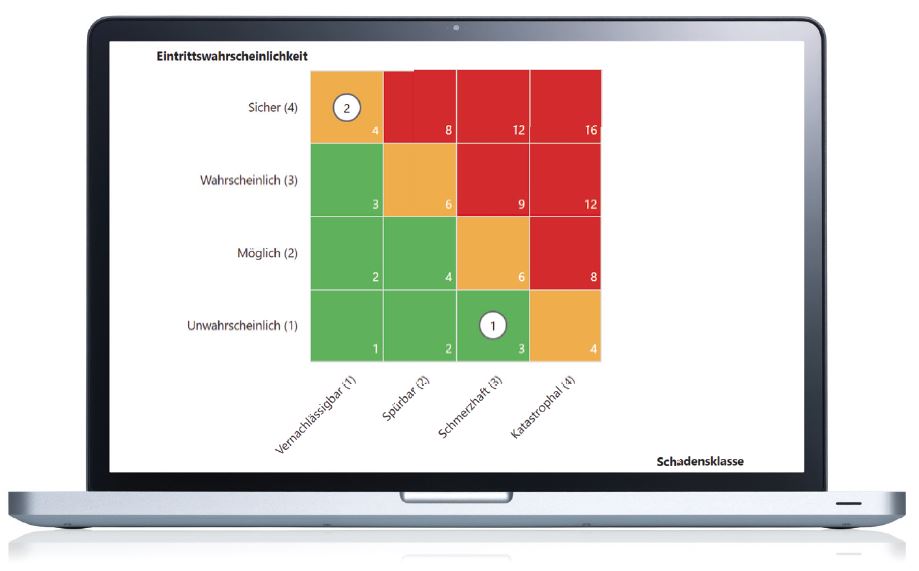
This step initiates a risk analysis for all assets that require a high level of protection. You will receive a number of sample templates and questionnaires for this purpose, and will be guided systematically through the process in order to identify the potential hazards. Next, you can determine the risk and obtain recommended measures to address such risk. After prioritization and cost estimation, the result can be forwarded to the management for approval.
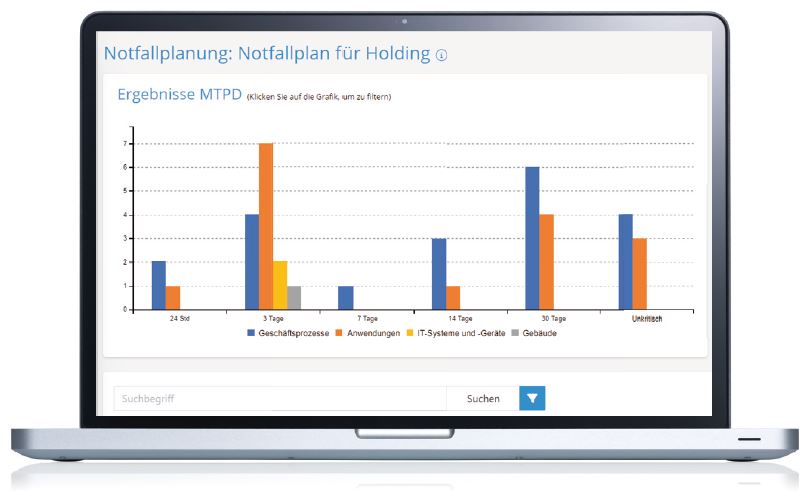
Conduct a business impact analysis to identify those business processes that are business critical for your organisation. You will be guided through the process with assistance. As a result, you will see the maximum tolerable downtime and recovery time for your assets. In the next step, create the recovery plan for the critical processes. The final emergency plan is created at the push of a button.
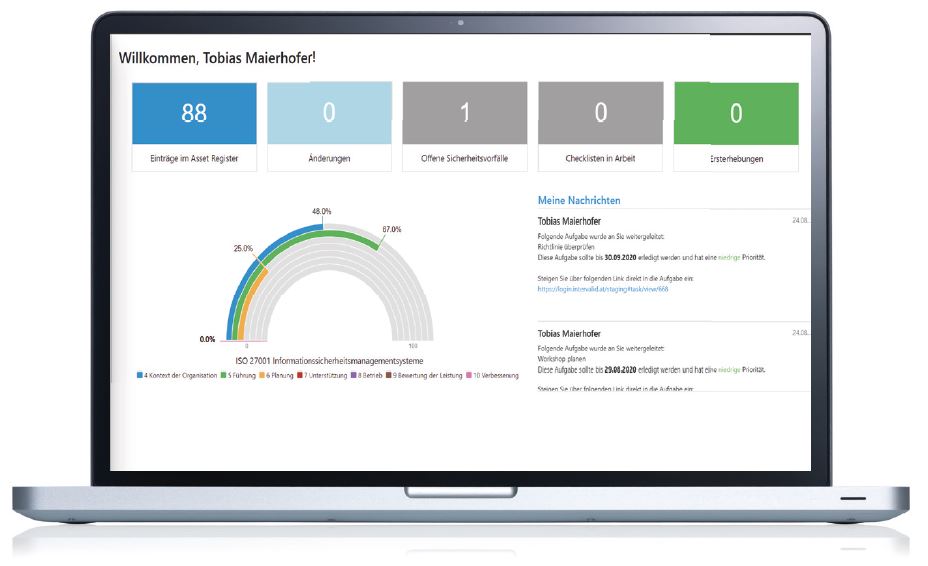
Create daily updated reports for internal or external information (e.g. audits, management reports, SoA, etc.) in the simple click of a button. The data can be exported via a CSV or a PDF file. This function allows you to monitor the current information security status of the company at any time, with all security incidents being documented transparently. The dashboard is configurable according to your requirements and provides a broad overview of the most important key data.
Use this function to respond to security incidents correctly and quickly: Record the key data, analyze the incident, inform all relevant departments in a timely manner and take preventive measures.
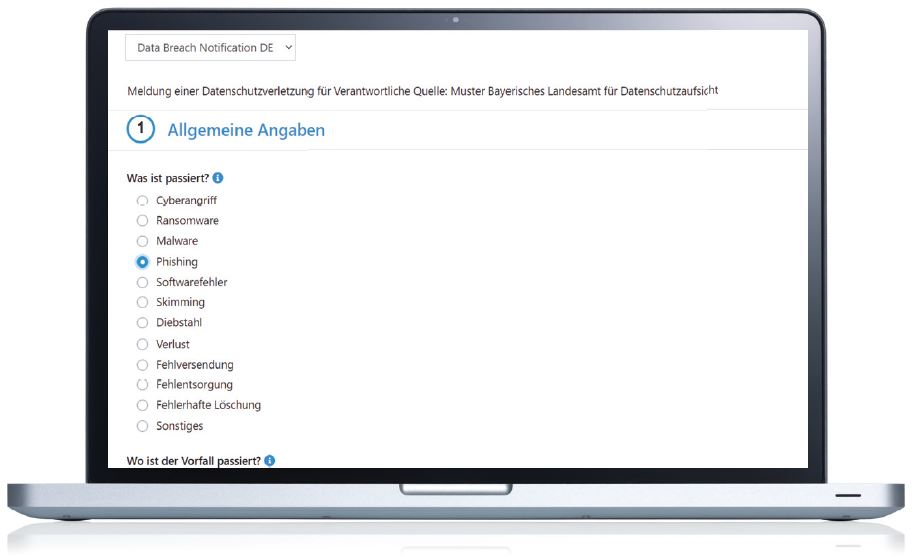
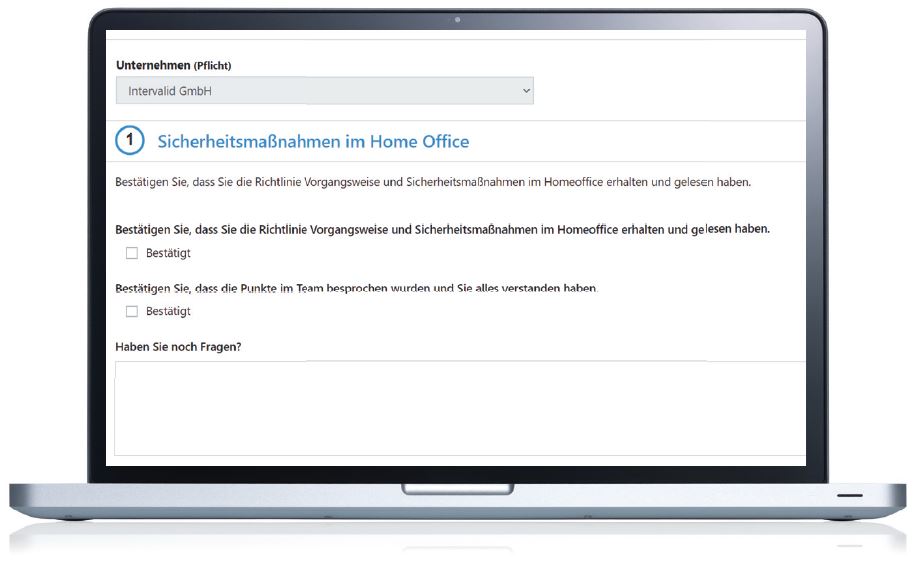
Obtain information about the current knowledge levels of your clients by sending out a template survey or a customized one. Once the survey has been completed, Intervalid produces a clear summary of the results, allowing you to see where there might be gaps in your client's knowledge. This function can also be used to easily confirm that the client and its employees have read and acknowledged the relevant policies.
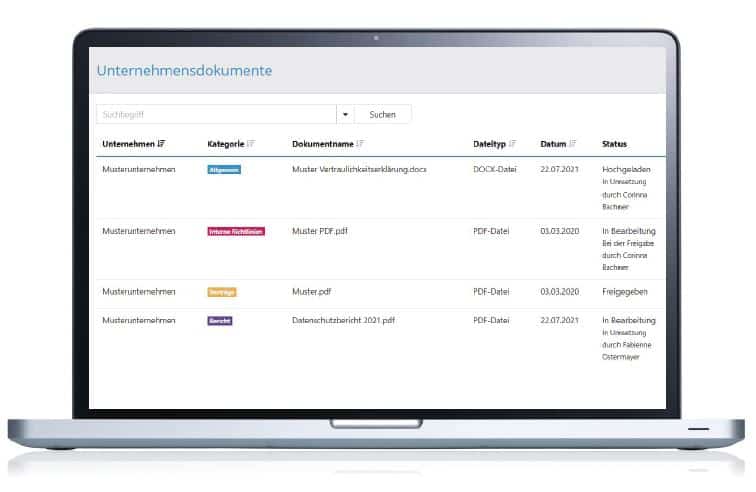
Create templates for corporate documents such as information security reports, policies, contracts and more. Numerous formatting options are available for this purpose and you can also use variables to automatically insert content into the document. The documents can then be forwarded to the responsible user for editing or approval. In this way, you are able to manage company documents centrally, are always aware of their status and can make them available to your clients.
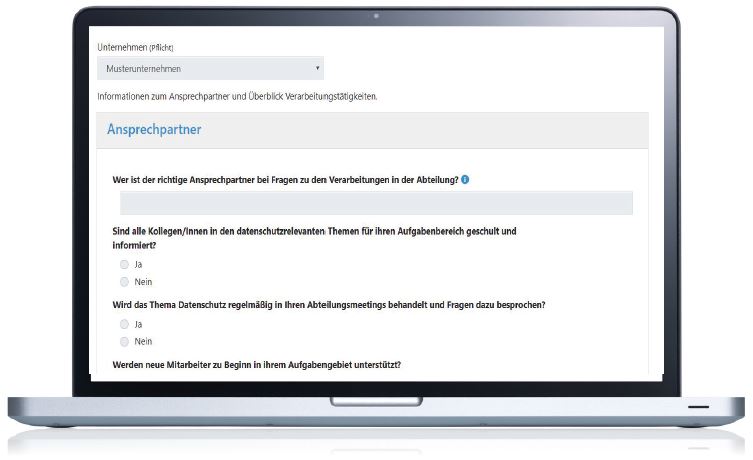
Questionnaires can be used to obtain important information from your clients quickly and efficiently. In particular, they can aid in documenting security incidents, carrying out risk analysis, classifying assets and customized ones can be created specifically for your needs. In addition, forms are helpful when introducing new assets or making changes to existing ones. These can be transferred directly to the register.
Supplier audits are used to check new or existing suppliers and processors in terms of information security compliance. The details of the contact person at the business partner will be entered and stored in the system and you can then send them a questionnaire or fill it out internally. After the form has been completed/returned, you can distribute tasks as required and complete the audit. Finally, a date can be set for the next audit.
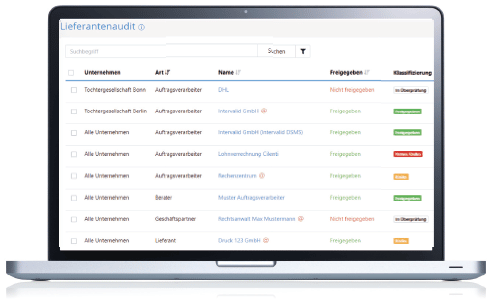
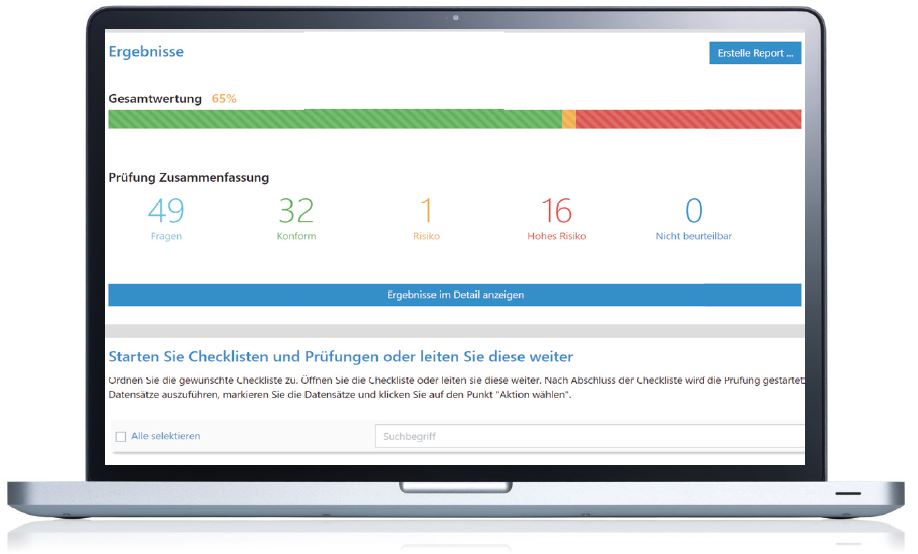
The establishment of an ISMS does not come to an end once the requisite measures have been implemented. It is a continuous process according to the Plan-Do-Check-Act method and therefore the effectiveness of the ISMS must be assessed regularly. Use the system's monitoring features to carry out an internal audit or to prepare for certification. Run through your business processes regularly, optimize if necessary, identify new risks and thus continuously minimize your business risk.
Get in touch to experience the benefits of Intervalid ISMS
Get in touch to experience the benefits of Intervalid ISMS
Copyright © 2020 Intervalid GmbH All rights reserved.
Contact us
We look forward to receiving your enquiry and are available:
Monday to Thursday from 08:30 am to 5:00 pm
and Fridays from 08:30 am to 3:00 pm.